There’s little that’s more important than protecting your database and the data/information within it. The most common form of “attack” comes from SQL injection and, even though monitoring systems vendors as well as your company’s IT staff are highly aware of how critical it is to protect your database from attack, it’s nevertheless difficult to catch problems when they’re small – and easier to fix before they can do damage to your business’ operations.
Database monitoring tools such as Apache Tomcat, can definitely help you keep an eye on your database, but using them alone won’t do enough to keep issues at bay. Regular monitoring of your database structure is key, and the proper setup of those monitoring tools and policies is critical to ensuring your monitoring is the best it can be
Read below for some of the best practices when it comes to setting up your database monitoring system:
1. Prioritize which data and transactions are the most critical to protect. To decide, talk to your developers and database administrators to ascertain where the most susceptible data is located and – this is critical – where the most important business information is located.
2. You’ll then need to inspect data application performance and the content of your database using discovery tools and database crawlers. Such monitoring can watch your sensitive data as it moves about in your system. Apache monitoring tools and others will find your critical data via both content and meta data analysis methods that will help you decide what needs protecting the most.
3. Watch your database transactions and SQL statements and do so over time. This will help you get an idea of how your particular database “works”: you’ll see what standard queries look like and you can then create and implement monitoring policies.
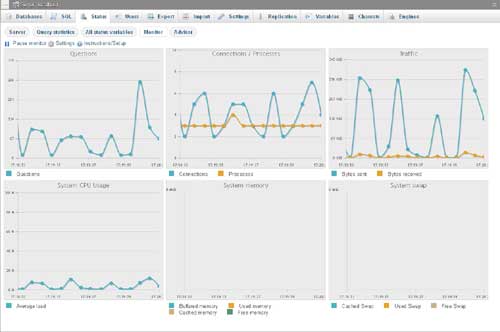
Figure 1. phpMyAdmin monitoring screen
4. Now it’s time to define what basic database security is for your system. At minimum, any database monitoring activity should include:
a. Monitoring and detection
b. Alerting and reporting
c. Verification of legitimation work orders and identifying misuse
d. SQL capture for inspecting
5. You’ll then need to set an arbitrary value to such examination characteristics as, for example:
a. Who the user is
b. What columns the user is looking at
c. The application being used
d. The amount of data touched
e. The time of day
6. By giving an arbitrary value to characteristics such as those mentioned above, your monitoring program will send alerts and warnings when someone accesses them (without permission) or, if the user has permission, exceeds them.
7. Lastly, when it comes to setting up who has access to what in regards to database monitoring, it’s wise from both a compliance and security standpoint to separate duties. Those who write the policies and review reports shouldn’t be assigned to also manage the monitored databases. In other words, it’s smart to create internal checks and balances.


Database monitoring tools such as Apache Tomcat, can definitely help
you keep an eye on your database
sounds like BS, sorry.