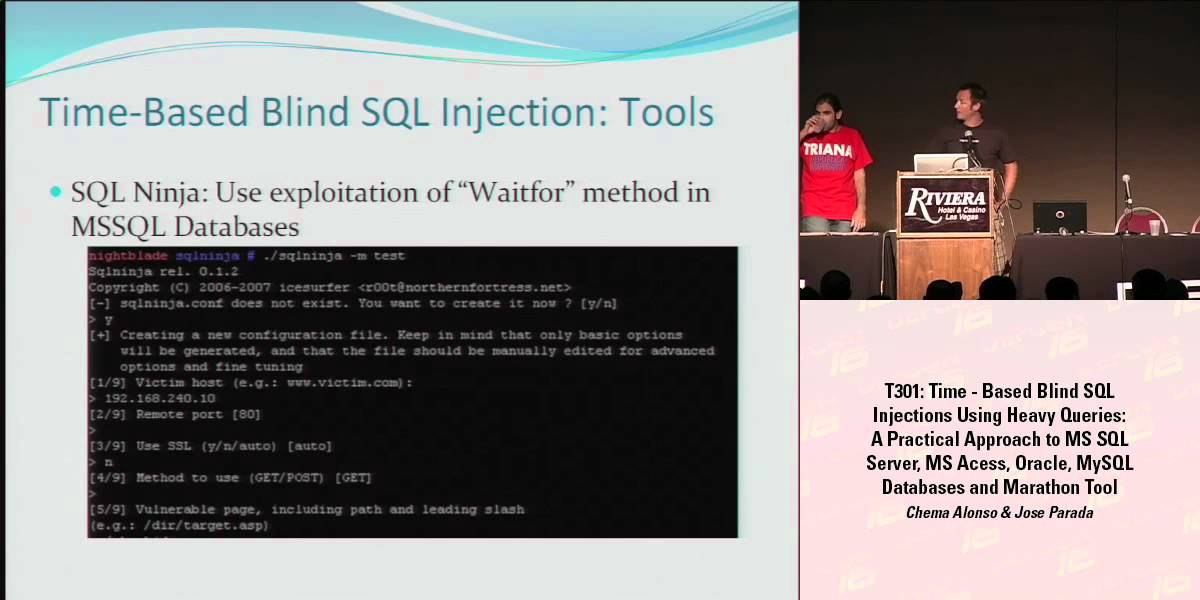
This presentation describes how attackers could take advantage of SQL Injection vulnerabilities using time-based blind SQL injection. The goal is to stress the importance of establishing secure development best practices for Web applications and not only to entrust the site security to the perimeter defenses. This article shows exploitation examples for some versions of Microsoft SQL Server, Oracle DB Engine, MySQL and Microsoft Access database engines, nevertheless the presented technique is applicable to any other database product in the market.
[youtube IwPS98RxdtI]
Video Producer: http://www.defcon.org/